Detecting OpenSSL CCS Injection Vulnerability (CVE-2014-0224)
Recently another major bug was found in OpenSSL library, CVE-2014-0224. Masashi Kikuchi discovered the vulnerability and has ellaborated here on how he discovered the vulnerability. This bug doesn’t have repercussions as Heartbleed bug, but still severe enough to patch the systems running vulnerable OpenSSL versions. There are many blog entries discussing this bug in detail, but over here I would like to put some light on how to detect this bug in the OpenSSL implementation on your own .
Without going into to much detail about how SSL works, the whole vulnerability and its exploit can be summarised as, if a CCS packet is sent before the master secret for an SSL session is calculated, the master secret is based on a weak pre-master secret and hence easily guessable and easy prey for a MITM attack.
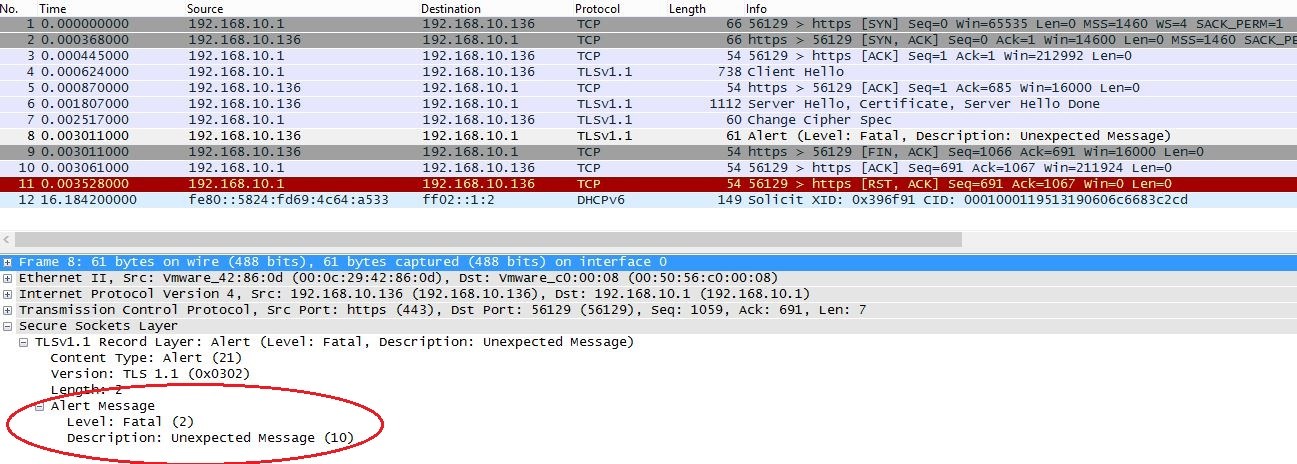
In case of version suffering with this vulnerability, if you send Cipher Change Spec (CCS) packet after completing the client hello, server hello, server certificate and server hello done step, you wont receive any SSL alert packet. The remote connection will still be open and listening. While in case of any patched version of OpenSSL, if you send CCS packet out of its sequence, in present case after server hello done, you will receive a fatal SSL alert packet for ‘Unexpected Message’. Below is a screenshot of a Wireshark session and shows the flow of packets and how does the Alert message looks like.
This scenario can be easily scripted and used to test against the various installation you might have. The Nmap script is available here.
Happy scripting!!